Intercepting web traffic with Zed Attack Proxy
We can use the Zed Attack proxy to intercept traffic of an application being tested. This post discusses how we can configure the proxy ports of Zed Attack Proxy to achieve this task. This post will list out the steps to achieve our tasks.
Assume we have a web application deployed on an apache tomcat server and that server is running on port 8080. Within the server.xml your configurations would look as below
<!-- A "Connector" represents an endpoint by which requests are received
and responses are returned. Documentation at :
Java HTTP Connector: /docs/config/http.html (blocking & non-blocking)
Java AJP Connector: /docs/config/ajp.html
APR (HTTP/AJP) Connector: /docs/apr.html
Define a non-SSL HTTP/1.1 Connector on port 8080
-->
<Connector port="8080" protocol="HTTP/1.1"
connectionTimeout="20000"
redirectPort="8443" />
and responses are returned. Documentation at :
Java HTTP Connector: /docs/config/http.html (blocking & non-blocking)
Java AJP Connector: /docs/config/ajp.html
APR (HTTP/AJP) Connector: /docs/apr.html
Define a non-SSL HTTP/1.1 Connector on port 8080
-->
<Connector port="8080" protocol="HTTP/1.1"
connectionTimeout="20000"
redirectPort="8443" />
Next, we need to configure Zed Attack Proxy to listen on a 8080 port, to achieve this visit Tools > Options > Local Proxy and set the configurations as shown below.
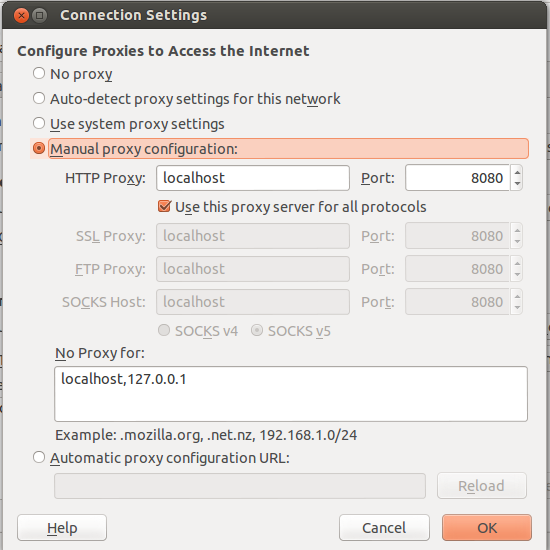
Next, we need to set the browser to communicate within the same port as shown below.
As a final step, access the application within tomcat using http://localhost:8080/appname and navigate the different areas of the application. This will result in Zed Attack Proxy capturing all the request that goes through the application.
As shown below the "sites" tree will be populated with all the pages captured by the proxy
We can then select any page listed from the sites and run any attack through the Zed Attack Proxy.


Comments
Post a Comment